Protect Your Inbox

We all need effective email security strategies to combat spam emails that waste our time. This guide provides best practices for email security tailored for retailers.
How Spammers Find Your Business Email
Public Listings You Can’t Avoid
Your email address often appears in mandatory business records, such as:
- ASIC company registrations (required for all Australian businesses)
- Domain registration details (when you buy a website domain)
- Industry directories (e.g., local chamber of commerce listings)
Your email addresses are often exposed through normal online activities. Spammers deploy automated programs called harvesters that scan websites, forums, and directories overnight. They can collect thousands of Australian business email addresses in a night's work.
Guessing Game Tactics
Guessing is often not hard, as most email addresses follow a typical pattern.
For example, if you are John Smith and work for "Your Business Pty Ltd," spammers will automatically try.
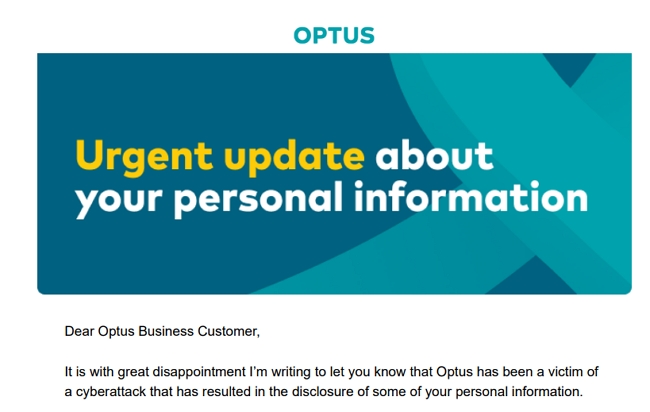
If your name is not known, what the spammer wants is that they assume that a small business uses [email protected] and use their list of the 40 common names (male and female) and send 40 emails. In Australia, approximately 13.6% of male newborns received one of the top 20 most popular names in 2023. Females are a bit higher with 14.36%, so they have a 10% chance of getting it. On a harvester program, this is not hard to do.
POS Systems
Your POS System receipts can be used too,
Buying lists
The primary reason for these massive data breaches is the thriving market for stolen email addresses. According to the Australian Cyber Security Centre, over 4 million Australian email credentials were compromised in breaches during 2024 alone. Spammers purchase these lists; I saw one on offer on the dark web marketplace containing additional information like names, companies, and email addresses for $US 100 per 100,000 addresses.
Simple ideas for retailers
Now that you understand how many spammers target your business emails, let's explore practical countermeasures you can implement immediately without disrupting your daily operations. These are not solutions, but they do help.
Switch to role-based Email Addresses.
Replace personal emails like john@ with functional addresses:
[email protected] (customer enquiries)
[email protected] (technical issues)
These sorts of addresses do not seem to interest spammers a lot.
A bonus is that it maintains continuity if staff leave or change roles.
Basic Email Masking
These do work, but it's a judgment decision, as often, they can confuse legitimate people with whom you want to give your email address with spammers.
Write addresses not as john@@yourbusiness.com.au but as john[at]yourbusiness[dot]com.au
On social media, use the Message buttons instead of posting emails.
Feature a phone number as the primary contact method.
Turn On the Free Spam Filters
All major email platforms include built-in protections, and these are excellent email security gateways.
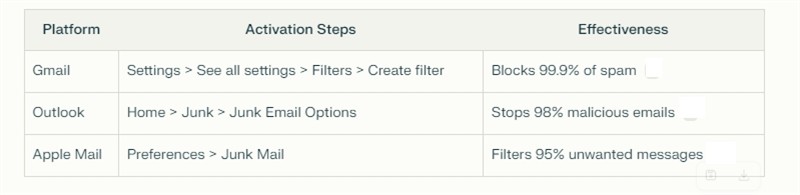
I tested Gmail with some of the latest email phishing attacks and was very pleased with how many it picked up. One particularly pleased me as it was a scam email from Microsoft, which I was sure it would not pick up, but it did.
Pro tip
Mark suspicious emails as spam instead of deleting them, as this trains your provider’s filters to improve accuracy.
Go into the spam folder and check those emails that are not spam.
Use Disposable Addresses
This method works but can cause problems for people who want your email address.
You create a temporary email for specific needs and then delete it. For example, for Mother's Day you could have set up an email address [email protected]
Next Steps for Immediate Protection
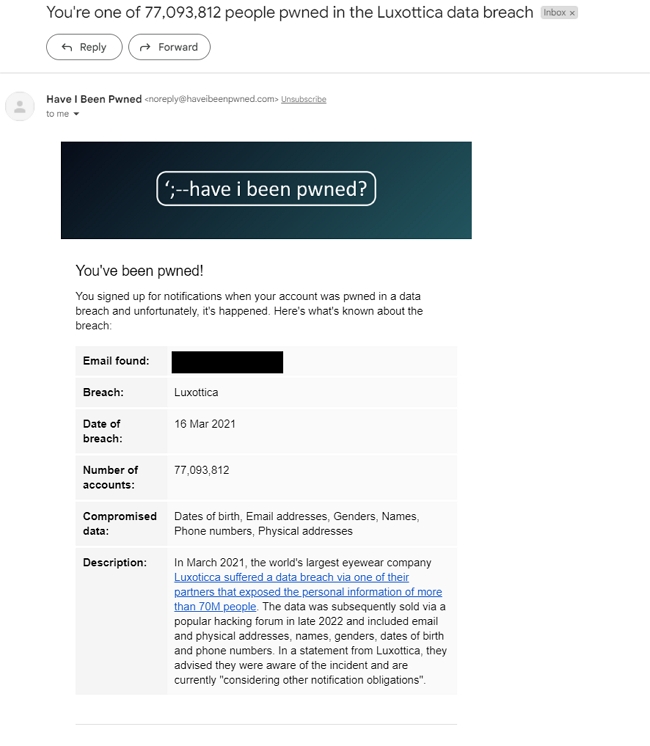
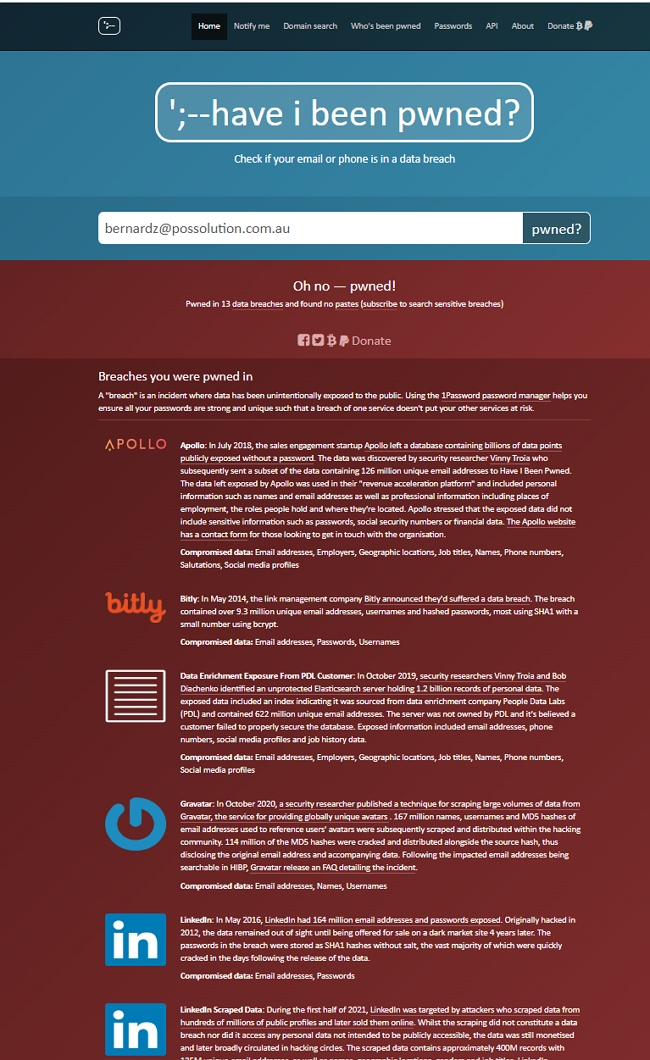
Use free tools like HaveIBeenPwned to see if your email is compromised. I have spoken about it here.
Conclusion
While spam will not disappear anytime soon, implementing the abovementioned strategies can dramatically reduce your exposure and protect your retail business from harmful attacks.
Written by:

Bernard Zimmermann is the founding director at POS Solutions, a leading point-of-sale system company with 45 years of industry experience. He consults to various organisations, from small businesses to large retailers and government institutions. Bernard is passionate about helping companies optimise their operations through innovative POS technology and enabling seamless customer experiences through effective software solutions.