Discussion on the Shoplifting Surge now
I was recently invited to listen to a compelling discussion about shoplifting issues in Britain here.
The parallels to the Australian retail landscape are striking, highlighting the global nature of these challenges. Let's explore the key points that I thought were particularly interesting and their relevance to our local context, focusing on effective strategies for retail loss prevention.
The Global Surge in Shoplifting
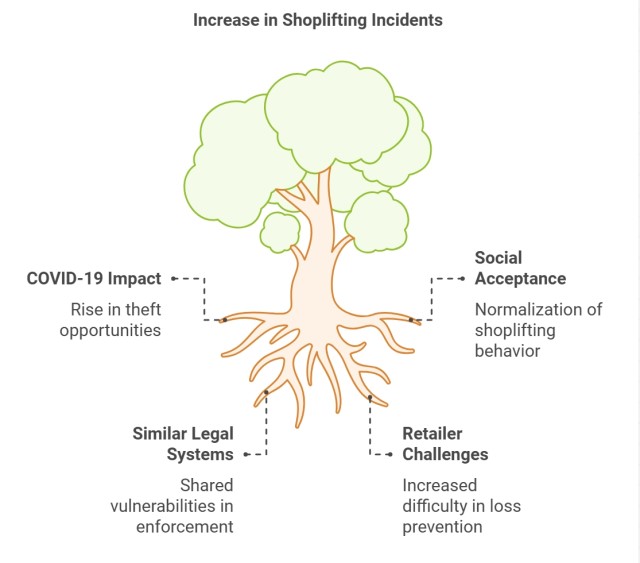
Although the discussion focused on Britain, I found it fascinating that many of the issues retailers face with shoplifters there are identical to what we're experiencing in Australia. This similarity isn't surprising, given our comparable societies and legal systems.
Just as I've reported here numerous times, Australian retailers have noted a sudden growth in shoplifting incidents since the onset of COVID-19. Interestingly, an identical pattern is in Britain.
One concerning observation is the apparent increase in social acceptance of shoplifting compared to a few years ago. This shift in public perception adds another layer of complexity to retailers' challenges.
The Crucial Role of Evidence in Loss Prevention
With the rise in shoplifting incidents, the importance of solid evidence has become even more critical. Several points from the discussion are particularly applicable here in Australia:
It's tough to secure a conviction for shoplifting without video or photographic evidence, so it would be best if you had it. Computer reports will only help a little as they're considered circumstantial evidence, making it very challenging to get a conviction based solely on such data.
Strategic Shop Analysis for Effective Security
A key strategy discussed was to analyse your shop layout from a potential shoplifter's perspective. Ask yourself: where would they likely strike? I've analysed how our POS Software can assist you in this process, which you can find here. I suggest that you draw such a map.
Leveraging POS Systems for Comprehensive Loss Prevention
Modern POS systems play a vital role in shoplifting prevention strategies:
- Real-time inventory tracking
- Customer behaviour analysis
- Identifying vulnerable areas in your store layout
These features provide a comprehensive approach to loss prevention, complementing physical security measures.
Advanced Security Technologies
The discussion highlighted AI-powered security cameras as a powerful tool in loss prevention. I was particularly impressed by their capabilities. These systems offer two key functionalities:
- Real-time alerts for suspicious behaviour
- Identification of known offenders upon entry
If you're considering upgrading your cameras, I recommend looking into these AI-enhanced systems. They're worth the investment for the added security they provide.
Effective Documentation Practices
Proper documentation is crucial when dealing with shoplifting incidents. While the British discussion recommended a special book, I think you should use email for documentation. Here's why:
- It automatically records the date and time
- It's easily searchable
- It creates a precise digital trail
Best Practice: When you provide information to law enforcement, please send it through official and email channels. This dual approach ensures you maintain a comprehensive record of communications. All too often in Australia, and apparently in Britain too, someone in the authorities might not act on the information you send or forget about it. With email records, you have proof of when you sent the information, protecting you from potential accusations of delay. It also makes it easy to keep a copy.
Conclusion
The rise in shoplifting requires a multifaceted approach to mitigate risks. While technology and best practices are crucial, we need some legal changes to address this growing issue more effectively.
Investing in a comprehensive security infrastructure is essential.
Have a listen to the discussion and let me know what you think, I welcome all comments.
Frequently Asked Questions (FAQ)
Q: How can I prevent shoplifting in my retail store?
A: I would start by looking at:
- Installing security cameras and electronic article surveillance systems
- Training staff on customer service and suspicious behaviour detection
- Optimizing store layout for better visibility
- Using security mirrors in blind spots
- Implementing a clear bag check policy
- Displaying anti-shoplifting signage
Q: What is the most effective deterrent to shoplifting?
A: The most effective deterrent combines visible security measures. This includes:
- Prominent security cameras
- Attentive staff
- Clear anti-theft signage
Q: What should I do when I catch someone shoplifting?
A: If you catch someone shoplifting:
- Stay calm and prioritise safety
- Use non-threatening language
- Document the incident thoroughly
- Contact the authorities if you have sufficient evidence
Q: Why do shoplifters use aluminium foil?
A: To make a "booster bag" or "magic bag" to beat security detectors; I have spoken about them here. If you use electronic article surveillance (EAS), I suggest you create a few booster bags to test your system. If you want you can buy them here.
Q: What happens when someone gets caught shoplifting?
A: Consequences can vary depending on local laws but may include:
- Being banned from the store. It isn't easy to do this without AI cameras.
- Fines or civil demands for damages
- Criminal charges and potential arrest
Q: What technology is used to prevent shoplifting?
A: Anti-shoplifting technology includes:
- AI-powered video analytics
- RFID inventory tracking
- Electronic Article Surveillance (EAS) systems
- Advanced POS systems with inventory management
- Facial recognition software (where legally permitted)
Q: How does AI stop shoplifting?
A: AI can help prevent shoplifting by:
- Analysing video feeds to detect suspicious behaviour
- Identifying known offenders through facial recognition
Q: What is the most common shoplifting method?
A: Common shoplifting methods include:
- Concealing items in bags, clothing, or strollers
- Swapping price tags or barcodes
- "Grab and run" tactics
- Using foil-lined bags to bypass EAS systems
- Leaving through emergency exits with unpaid merchandise
Q: What is loss prevention training?
A: Loss prevention training educates employees on:
- Identifying and preventing theft (both internal and external)
- Proper cash handling procedures
- Inventory management best practices
- Customer service techniques that deter shoplifting
- Emergency response protocols
Q: How can store layout prevent shoplifting?
A: Effective store layouts can prevent shoplifting by:
- Ensuring clear sightlines throughout the store
- Positioning high-value items in visible, monitored areas
- Placing checkout counters near exits
- Using appropriate shelving heights to maintain visibility
- Implementing an organised and clutter-free environment
Q: What are loss prevention policies?
A: They typically cover:
- Shoplifting prevention strategies
- Employee theft deterrence
- Inventory management procedures
- Cash handling protocols
- Emergency response plans